roadscene2vec: A Tool for Extracting and Embedding Road Scene-Graphs
Corresponding Author: Arnav Malawade (malawada@uci.edu)
Citation Authors: Arnav Malawade, Shih-Yuan Yu, Brandon Hsu, Harsimrat Kaeley, Anurag Karra, Mohammad Al Faruque
Access Link: Github
Paper Link: arXiv
Language: Python
License: Creative Commons Attribution
Keywords: scene-graph, graph embedding, autonomous vehicle, vehicle safety, graph learning, knowledge graph
Abstract
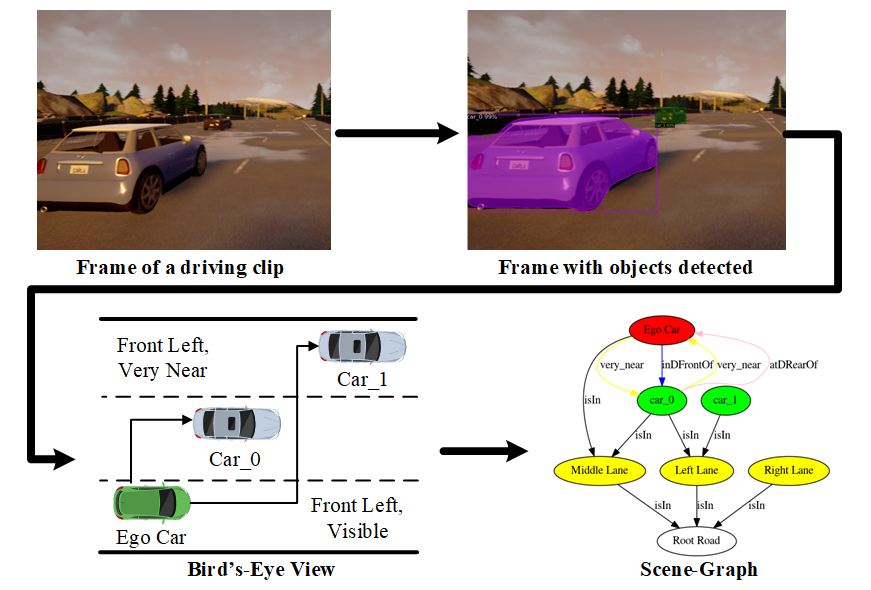
Recently, road scene-graph representations used in conjunction with graph learning techniques have been shown to outperform state-of-the-art deep learning techniques in tasks including action classification, risk assessment, and collision prediction. To enable the exploration of applications of road scene-graph representations, we introduce roadscene2vec: an open-source tool for extracting and embedding road scene-graphs. The goal of roadscene2vec is to enable research into the applications and capabilities of road scene-graphs by providing tools for generating scene-graphs, graph learning models to generate spatio-temporal scene-graph embeddings, and tools for visualizing and analyzing scene-graph-based methodologies. The capabilities of roadscene2vec include (i) customized scene-graph generation from either video clips or data from the CARLA simulator, (ii) multiple configurable spatio-temporal graph embedding models and baseline CNN-based models, (iii) built-in functionality for using graph and sequence embeddings for risk assessment and collision prediction applications, (iv) tools for evaluating transfer learning, and (v) utilities for visualizing scene-graphs and analyzing the explainability of graph learning models. In our paper, we demonstrate the utility of roadscene2vec for these use cases with experimental results and qualitative evaluations for both graph learning models and CNN-based models. On our Github repository, we provide links to our carla scene-graph datasets for use with our tool. Please cite our paper if you find our tool or data useful for your research.
Hardware Design Dataset for Circuit Graph Learning
Corresponding Author: Rozhin Yasaei (ryasaei@uci.edu)
Citation Authors: Rozhin Yasaei, Shih-Yuan Yu, Mohammad Abdullah Al Faruque
Access Link: IEEE-Data port
License: Creative Commons Attribution
Keywords: Hardware Security, Representation Learning, Graph Embedding
User Documents: supporting documents
Paper Citation and Link: Yu, Shih-Yuan, et al. “HW2VEC: A Graph Learning Tool for Automating Hardware Security.” arXiv preprint arXiv:2107.12328 (2021). Link
HW2VEC: Graph Learning Tool for Automating Hardware Security
Corresponding Author: Shih-Yuan Yu (shihyuay@uci.edu)
Citation Authors: Shih-Yuan Yu, Rozhin Yasaei, Mohammad Abdullah Al Faruque
Access Link: GitHub Repository
License: MIT License
Keywords: Hardware Security, Representation Learning, Graph Embedding
User Documents: supporting documents
Paper Citation and Link: Yu, Shih-Yuan, et al. “HW2VEC: A Graph Learning Tool for Automating Hardware Security.” arXiv preprint arXiv:2107.12328 (2021). Link
Abstract:
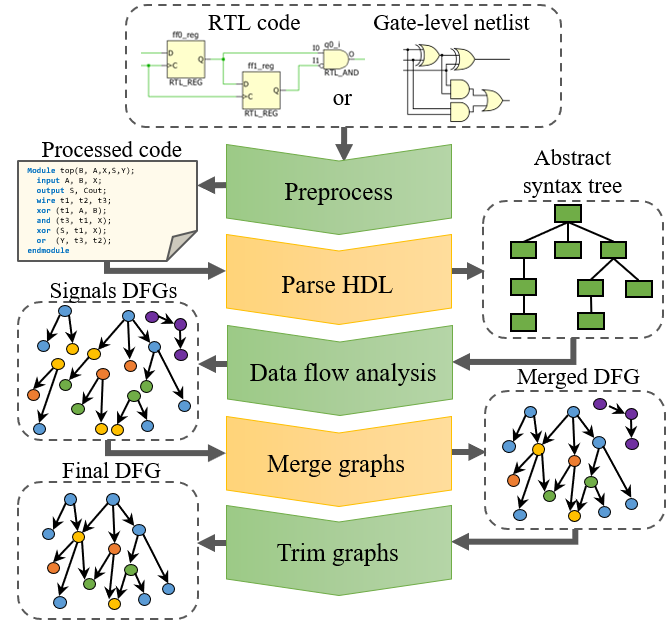
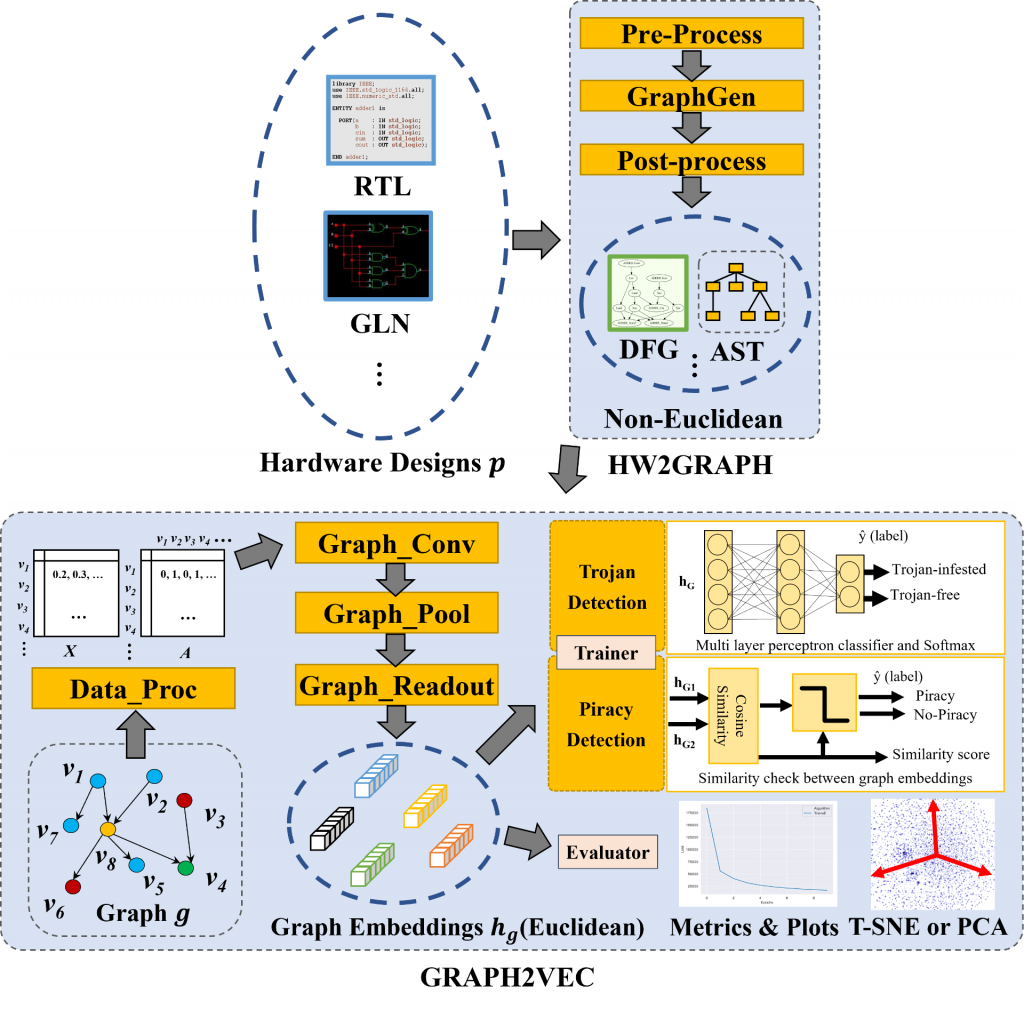
HW2VEC is an open-source graph learning tool for hardware security applications. HW2VEC provides an automated pipeline to extract a graph representation (abstract syntax tree or data flow graph) from a hardware design in various abstraction levels (RTL or gate-level netlist). Besides, HW2VEC includes graph learning functional components for users to apply graph learning approaches to these hardware designs in non-Euclidean form according to their problem settings. In this readme, we demonstrate how to use HW2VEC and provide its use-cases for two hardware security applications: Hardware Trojan Detection and IP Piracy Detection. We hope that HW2VEC can be helpful for researchers and practitioners in the hardware security research community. In this repo, we integrate Pyverilog as part of our graph extraction pipeline (HW2GRAPH) and Pytorch-Geometric into our graph learning pipeline (GRAPH2VEC).
Pykg2vec: A Python Library for Knowledge Graph Embedding
https://github.com/Sujit-O/pykg2vec
Corresponding Author: Shih-Yuan Yu (shihyuay@uci.edu)
Access Link: GitHub Repository
License: MIT License
Keywords: Knowledge Graph Embedding, Representation Learning.
Abstract:
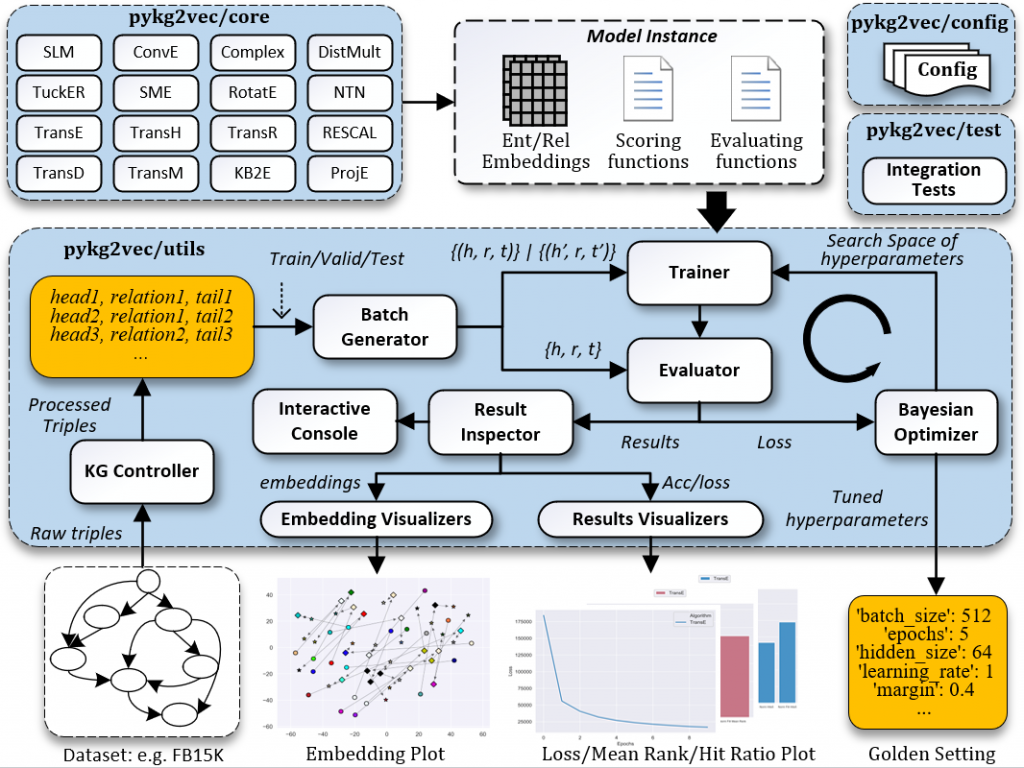
Pykg2vec is a Python library for learning the representations of the entities and relations in knowledge graphs. Pykg2vec’s flexible and modular software architecture currently implements 25 state-of-the-art knowledge graph embedding algorithms and is designed to easily incorporate new algorithms. The goal of pykg2vec is to provide a practical and educational platform to accelerate research in knowledge graph representation learning. Pykg2vec is built on top of PyTorch and Python’s multiprocessing framework and provides modules for batch generation, Bayesian hyperparameter optimization, evaluation of KGE tasks, embedding, and result visualization. Pykg2vec is released under the MIT License and is also available in the Python Package Index (PyPI)
– For further information, see the supporting documents.
– Please cite the following papers when using any data from this dataset:
Yu, Shih-Yuan, et al. “Pykg2vec: A Python Library for Knowledge Graph Embedding.” J. Mach. Learn. Res. 22 (2021): 16-1. Link.
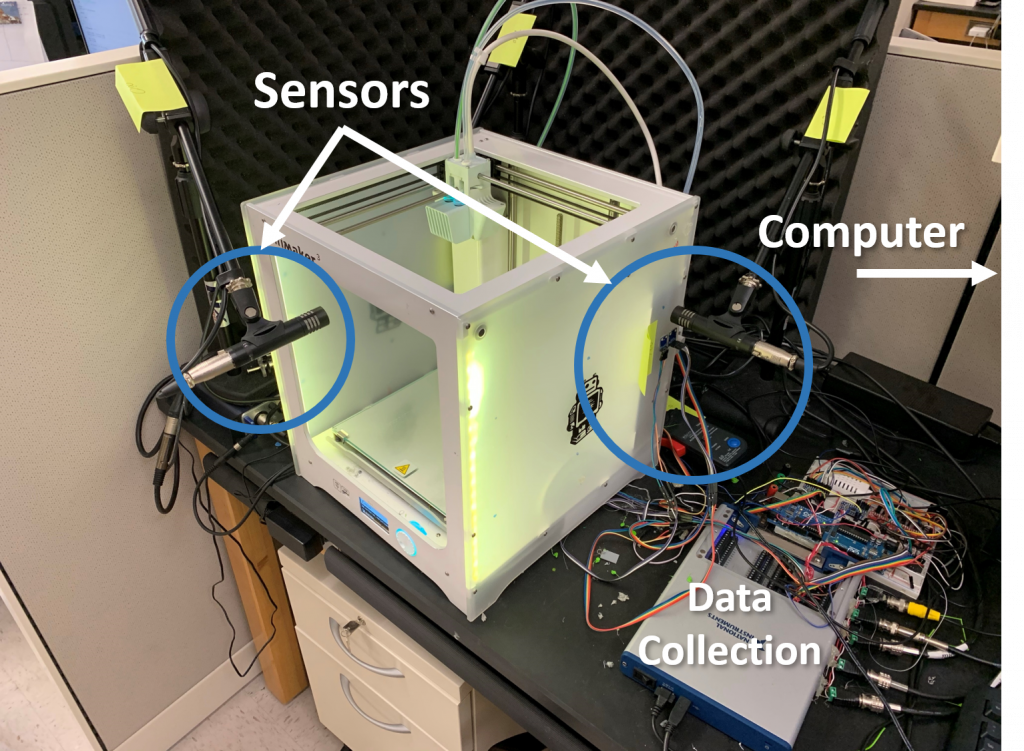
SideChannel-3D: Acoustic, Vibration, Magnetic, and Power Side-Channel 3D Printer Dataset
Corresponding Author: Arnav Malawade (malawada@uci.edu)
Citation Authors: Nathan Costa, Shih-Yuan Yu, Arnav Malawade, Sujit Chhetri, Mohammad Al Faruque
Access Link: IEEE-Dataport
DOI: 10.21227/j6cw-y314
Data Format: *.csv; *.tdms; *.stl; *.mp4
License: Creative Commons Attribution
Keywords: manufacturing, 3D printer, additive manufacturing, sabotage attack, side-channel, security, cyber-physical systems, digital twin, acoustic emission, vibrations, electromagnetics
Abstract:
This dataset contains multimodal sensor data collected from side-channels while printing several types of objects on an Ultimaker 3 3D printer. Our related research paper titled “Sabotage Attack Detection for Additive Manufacturing Systems” can be found here: https://doi.org/10.1109/ACCESS.2020.2971947. In our work, we demonstrate that this sensor data can be used with machine learning algorithms to detect sabotage attacks on the 3D printer. By utilizing multiple side-channels, we improve system state estimation significantly in comparison to uni-modal techniques. Besides, in the paper we analyze the value of each side-channel for performing attack detection in terms of mutual information shared with the machine control parameters. We evaluate our system on real-world test cases and achieve an attack detection accuracy of 98.15%. Our dataset contains sets of G-codes synchronized with the corresponding sensor readings and sensor features, enabling highly accurate state estimation. This state estimation capability can be useful for tasks such as security, predictive maintenance, quality control, automated calibration, etc.
Our testbed contains the following types and quantities of sensors placed in various locations around the 3D printer:
- 3x 3-axis magnetometer.
- 3x 3-axis accelerometer.
- 4x high-definition microphone.
- 1x DC current clamp.
- internal sensor data from the 3D printer.
Please kindly consider citing our paper if you find this dataset useful for your research.
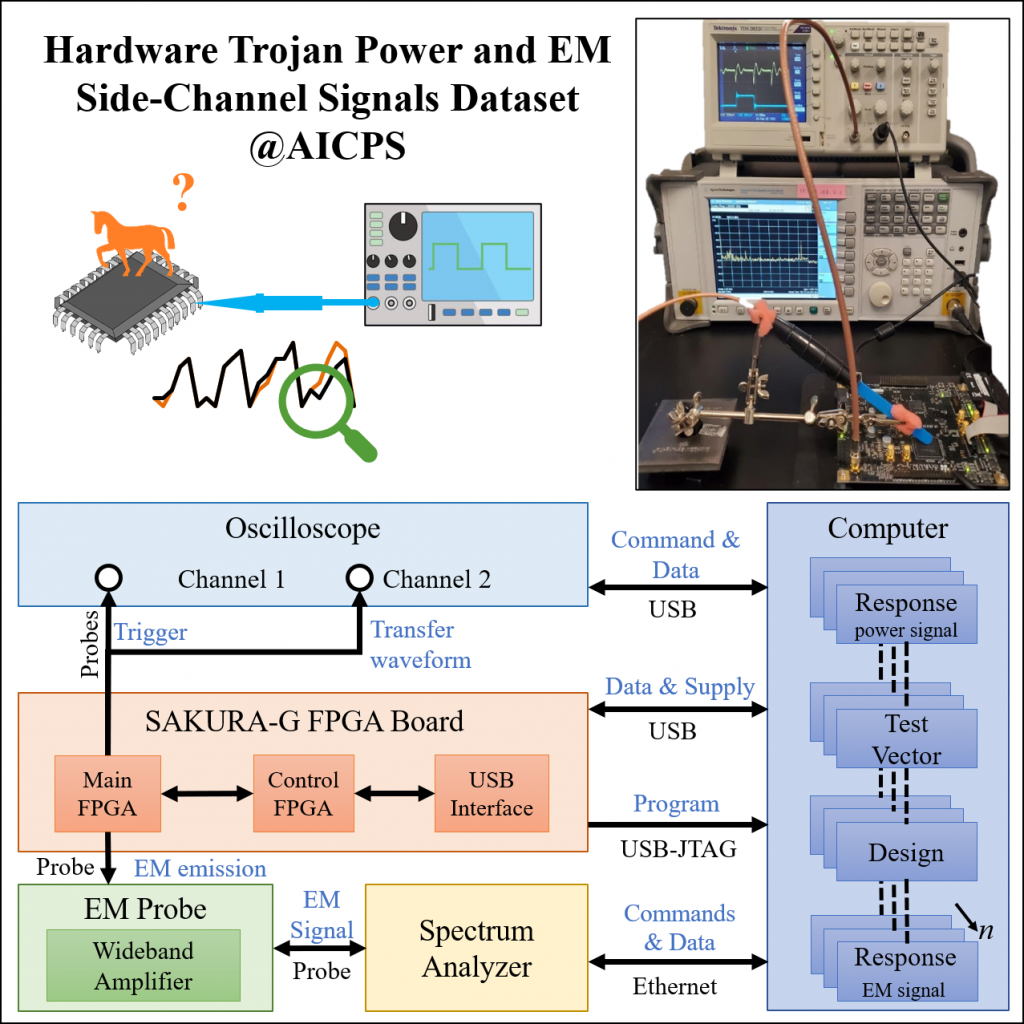
Power and EM Side-Channel for Hardware Trojan Dataset
Corresponding Author: Rozhin Yasaei (ryasaei@uci.edu)
Citation Authors: Rozhin Yasaei, Sina Faezi, Mohammad Abdullah Al Faruque
Access Link: IEEE-Dataport
DOI: 10.21227/9fwb-8978
Data Format: *.csv
License: Creative Commons Attribution
Keywords: Side-Channel Signal, Power Consumption, Electromagnetics, Hardware Trojan, Hardware Security.
Abstract:
Design and fabrication outsourcing has made integrated circuits vulnerable to malicious modifications by third parties known as hardware Trojan (HT). Over the last decade, the use of side-channel measurements for detecting the malicious manipulation of the chip has been extensively studied. However, the suggested approaches mostly suffer from two major limitations: reliance on trusted identical chip (e.i. golden chip); untraceable footprints of subtle hardware Trojans which remain inactive during the testing phase. To overcome these shortcomings, we propose a novel idea of maintaining a dynamic model of the integrated circuit throughout its life cycle for the purpose of detecting HT that might have been injected anywhere in the supply chain. In this paper, we gather a comprehensive dataset of power and Electromagnetic (EM) side-channel signals for hardware Trojan benchmarks from Trust Hub benchmarks to develop a statistical model of the chip for HT detection. To be used in a golden chip-free Trojan detection approach, the side-channel data is collected in the presence of HT under two scenarios: when the HT is inactive and when it is activated. Consequently, all the measured power data include the static power of HT in addition to base circuit power consumption, which makes the detection more challenging. The only difference between the two data collection scenarios is the dynamic power consumption of HT.
– For further information, see the supporting documents.
– Please cite the following papers when using any data from this dataset:
Faezi, Rozhin Yasaei, Anomadarshi Barua, Mohammad Abdullah Al Faruque, “Brain-Inspired Golden Chip Free Hardware Trojan Detection”, IEEE Transaction on Information Forensics and Security (IEEE TIFS’21), 2021.
– This research was supported by the Office of Naval Research (ONR) award N00014-17-1-2499.
Scenegraph-Risk-Assessment Dataset
Corresponding Author: Shih-Yuan Yu (shihyuay@uci.edu)
Citation Authors: Brandon Hsu, Shih-Yuan Yu, Arnav Malawade, Deepan Multhirayan, Pramod Prabhakar, Mohammad Abdullah Al Faruque
Access Link: IEEE-Dataport
Keywords: Scene-Graph Embedding, Autonomous Vehicle, Risk Assessment.
Abstract:
This dataset is released with our research paper titled “Scene-graph Augmented Data-driven Risk Assessment of Autonomous Vehicle Decisions” (https://arxiv.org/abs/2009.06435). In this paper, we propose a novel data-driven approach that uses scene-graphs as intermediate representations for modeling the subjective risk of driving maneuvers. Our approach includes a Multi-Relation Graph Convolution Network, a Long-Short Term Memory Network, and attention layers. To train our model, we formulate the problem of subjective risk assessment as a supervised scene classification problem. We evaluate our model on both synthetic lane-changing datasets and real-driving datasets with various driving maneuvers. We show that our approach achieves a higher classification accuracy than the state-of-the-art approach on both large (96.4% vs. 91.2%) and small (91.8% vs. 71.2%) lane-changing synthesized datasets, illustrating that our approach can learn effectively even from small datasets. We also show that our model trained on a lane-changing synthesized dataset achieves an average accuracy of 87.8\% when tested on a real-driving lane-changing dataset. In comparison, the state-of-the-art model trained on the same synthesized dataset only achieved 70.3% accuracy when tested on the real-driving dataset, showing that our approach can transfer knowledge more effectively. Moreover, we demonstrate that the addition of spatial and temporal attention layers improves our model’s performance and explainability. Finally, our results illustrate that our model can assess the risk of various driving maneuvers more accurately than the state-of-the-art model (86.5% vs. 58.4%, respectively).
In this dataset, we release both synthetic and real-driving scene-graph risk assessment datasets (e.g. syn-271-sg, syn-1043-sg, honda-571-sg, honda-1361-sg) and synthetic video clip datasets (syn-271-image, syn-1043-image) for helping our users reproduce the results presented in our paper. Our source code is available on Github (https://github.com/louisccc/sg-risk-assessment). Please kindly consider citing us if you find this dataset useful in your research.
GridMat: A Matlab/Simulink Toolbox for GridLAB-D
Corresponding Authors: Mohammad Abdullah Al Faruque, Korosh Vatanparvar
Download link: SourceForge
Tool Overview:
Modeling a complex, large-scale, heterogeneous, multi-physics, multi-domain, and distributed system like microgrid requires heterogeneous composition of physical, computational, and communication sub-systems including their causality, time semantics, and different physical domains.
State-of-the-art distribution grid and/or microgrid modeling & simulation tools are domain-specific and are mostly capable to capture only the physical components (power system and energy resources) of the model. However, common to most of the tools is that these tools do not provide a test bed to simulate an energy distribution model like residential microgrid where power system modeling at a very detailed level, e.g. at appliance level is required. To solve this problem of modeling detailed residential power systems of a residential microgrid, we have used GridLAB-D, an agent-based power system modeling and simulation tool.
Existing power system modeling tools including GridLAB-D lack the capability to capture the cyber-components (control, software, communication, and embedded hardware) during modeling and simulation. Therefore, new methodology and/or tools are required to integrate various domain-specific tools.
In this project, we are following a model-based design approach. We have developed a Matlab/Simulink toolbox for GridLAB-D that supports modeling, simulation, grid impact analysis, and validation of power & control systems of a residential microgrid. Details will come soon.
– Related Publications:
- M. A. Al Faruque, F. Ahourai: “GridMat: Matlab Toolbox for GridLAB-D to Analyse Grid Impact and Validate Residential Microgrid Level Energy Management Algorithms”, accepted to be published in IEEE PES Conference on Innovative Smart Grid Technologies (ISGT’14), Washington DC, USA, February 2014. (Premier conference for smart grid research)
- F. Ahourai, I. Huang, M. A. Al Faruque: “Modeling and Simulation of the EV Charging in a Residential Distribution Power Grid”, accepted to be published in IEEE Green Energy and Systems Conference (IGESC’13), California, US, November 2013
- M. A. Al Faruque, F. Ahourai: “A Model-based Design of Cyber-Physical Energy Systems”, accepted to be published in IEEE/ACM 19th Asia and South Pacific Design Automation Conference (ASP-DAC’14), Singapore, January 2014.
- F. Ahourai, M. A. Al Faruque: “Grid Impact analysis of a Residential Microgrid under Various EV Penetration Rates in GridLAB-D“, Technical Report, TR 13-08, July 2013. download pdf
– For referring to this tool please use the following publication:
M. A. Al Faruque, F. Ahourai: “GridMat: Matlab Toolbox for GridLAB-D to Analyse Grid Impact and Validate Residential Microgrid Level Energy Management Algorithms”, accepted to be published in IEEE PES Conference on Innovative Smart Grid Technologies (ISGT’14), Washington DC, USA, February 2014.