Introduction
Our security work mostly involves cross-layer and cross-domain security issues for various embedded and cyber-physical systems including automotive, transportation systems, manufacturing, Internet-of-Things, smart grid, etc. Below few of our current research highlights are given.
Research Area 1: Internet of Things (IoT) Security
Rozhin Yasaei (contact person)
The deployment of Internet of Things (IoT) devices in cyber-physical applications has introduced a new set of vulnerabilities. The new security and reliability challenges require a holistic solution due to the cross-domain, cross-layer, and interdisciplinary nature of IoT systems. However, the majority of works presented in the literature primarily focus on the cyber aspect, including the network and application layers, and the physical layer is often overlooked.
In this paper, we utilize IoT sensors that capture the physical properties of the system to ensure the integrity of IoT sensors data and identify anomalous incidents in the environment. We propose an adaptive context-aware anomaly detection method that is optimized to run on a fog computing platform. In this approach, we devise a novel sensor association algorithm that generates fingerprints of sensors, clusters them, and extracts the context of the system. Based on the contextual information, our predictor model, which comprises a Long-Short Term Memory (LSTM) neural network and Gaussian estimator, detects anomalies, and a consensus algorithm identifies the source of the anomaly. Furthermore, our model updates itself to adapt to the variation in the environment and system.
The results demonstrate that our model detects the anomaly with 92.0% precision in 532ms, which meets the real-time constraint of the system under test.
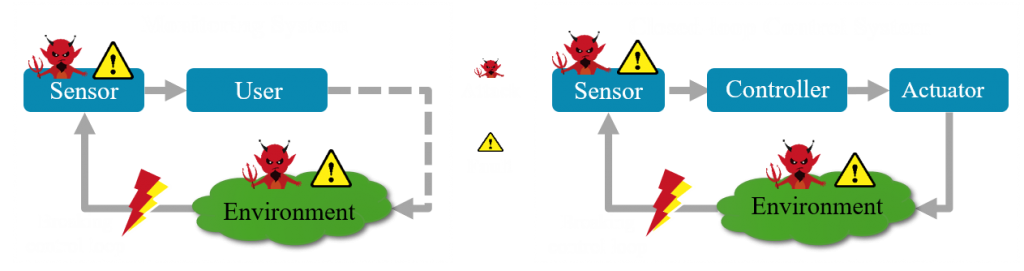
Environmental Anomaly (EA): The environment is the area that surrounds the sensor, and the sensor measures its physical properties. Any anomaly in the environment affects the measurements of the sensor and disrupts it. An EA may occur as a result of malicious activities or unexpected incidents in the environment.
Sensing Device Anomaly (SDA): When the operation of a sensor is corrupted, its measurements do not follow the same pattern, and an SDA is observed. This corruption occurs because of either security or reliability issues.
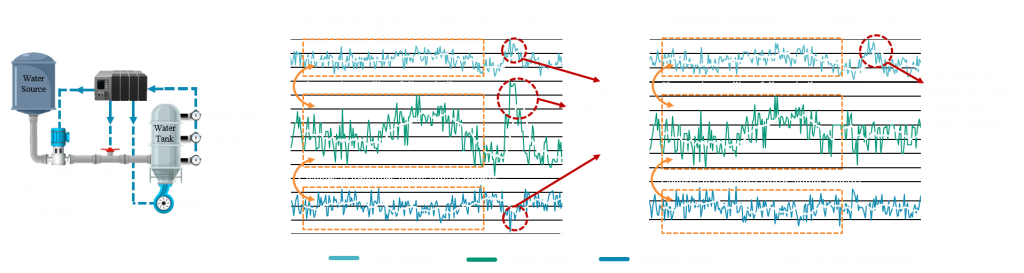
As a real-world IoT system, we study the environmental training center wastewater plant in Riccione \cite{wastewater}. The primary purpose of wastewater treatment is the elimination of nitrate. Nitrate contamination is a severe environmental problem because it can exhibit toxicity toward aquatic life, present a public health hazard, and affect the suitability of wastewater. In the treatment process, the wastewater is pumped to the tanks, which are equipped with sensors to monitor the concentration of oxygen, ammonia, and nitrate in the water. The actuators, such as blowers and valves, are controlled by a Programmable Logic Controller to adjust the level of chemicals.
Given the importance of the nitrate level, anomaly detection is applied to detect abnormal changes. Consider two scenarios with an anomalous rise in nitrate level; In the first scenario, environmental changes alter the water temperature, which affects the chemical reactions in the water tank (an example of EA). In the second scenario, the nitrate sensor is broken or manipulated by an attacker (an example of SDA). The current anomaly detection methods rely solely on nitrate sensor data, whereas the validity of its data is questionable. Thus, they can not find the source of anomaly and discriminate between EA and SDA.
A recent study analyzes the sensors of this wastewater plant and reveals the correlation between ammonia, oxygen, and nitrate sensor data. More specifically, when the rise in oxygen density reaches a certain threshold, the ammonia concentration decreases, and the nitrate concentration increases. Further investigation reveals the scientific rationale for this correlation; oxygen triggers the chemical reaction, which affects the ammonia and nitrate concentration. By considering this relationship, it is possible to validate sensor signals. In the first scenario, the incident affects all sensors. Despite irregularities in the sensor signals, they are consistent with each other. Thus, we can conclude that the integrity of the sensors’ data is not compromised. In the second scenario, the anomaly in the nitrate sensor data is inconsistent with the patterns of other sensor signals. It indicates that the cause of the abnormality is fault or attack. This type of relationship between sensors is not limited to this wastewater plant and it is observed in many IoT systems due to the availability of many heterogeneous sensors.
Our Contributions:
- Context-aware sensor association algorithm: We develop a multi-modality clustering method to associate sensors that experience similar contextual variation.
- Consensus-based strategy for unsupervised anomaly detection: We design a methodology to pinpoint anomalies without reliance on prior knowledge about possible anomalies.
- Adaptive data-driven model: Our proposed anomaly detection model is periodically updated at run-time to adapt itself to new states caused by variations in the system.
Research Area 2: Sensor Attack – Hardware/Software Codesign for Defense
Anomadarshi Barua (contact person)
Nowadays, different smart sensors and transducers are tightly integrated with the cyber-physical systems. This integration opens the “Pandora’s Box” of unknown threats that could come from very unconventional ways. Our research works include a wide range of sensor attacks, such as analog sensors, inertial sensors, active sensors, passive sensors, in different cyber-physical systems. Moreover, our research works also include different defense mechanisms against such attacks by exploring hardware/software codesign techniques.
One of our works shows that it is possible to spoof the hall sensors of a grid-tied inverter noninvasively with adversarial control. The spoofing can cause injection of errors into the hall sensor and these errors can propagate from the compromised hall sensor to the internal controllers of the inverter to compromise the inverter itself. The compromised inverter can hamper the grid stability and may cause grid failures in a weak grid scenario. The following figure depicts our novel attack model. This work is accepted in 29th USENIX Security, 2020.
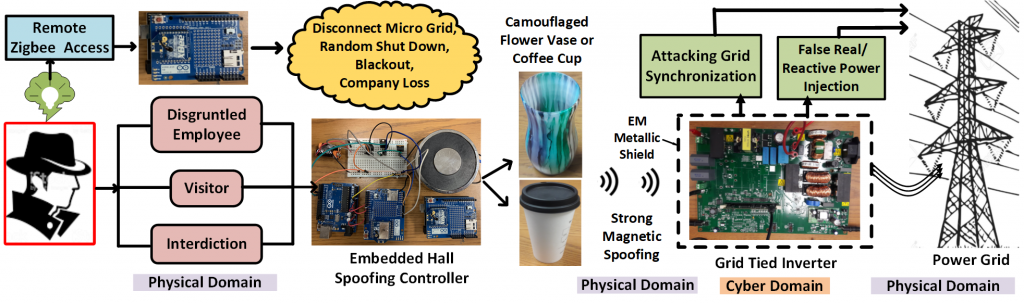
Our current research works involve finding the solutions to contain this unconventional spoofing attack inside of the sensors in real-time, so that the attack can not propagate farther to the connected sophisticated systems.
- A short video presentation on the sensor attack in power cyber-physical systems is given below:
Research Area 3: Machine Learning Model Stealing Attacks on GPU and FPGA
Yicheng Zhang (contact person), Rozhin Yasaei
Machine-learning has been attracting strong interests in recent years. Numerous companies have invested great efforts and resources to develop customized deep-learning models, which are their key intellectual properties. Our works include a wide range of different confidentiality, availability and integrity attacks on machine learning models on different platforms, such as CPUs, GPUs, and FPGAs.
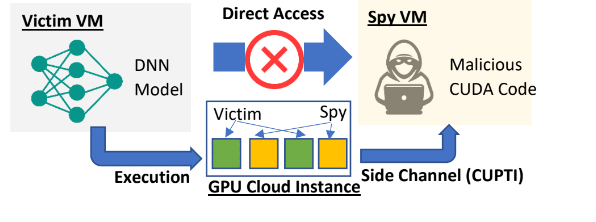
In one of our works, we investigate to what extent the secret of deep-learning models can be inferred by attackers. In particular, we focus on the scenario that a model developer and an adversary share the same GPU when training a Deep Neural Network (DNN) model. We exploit a new GPU side-channel based on context-switching penalties. This side-channel allows us to extract the fine-grained structural secret of a DNN model, including its layer composition and hyper-parameters. Leveraging this side-channel, we developed an attack prototype named MoSConS, which applies LSTM-based inference models to identify the structural secret. Our evaluation of MoSConS shows the structural information can be accurately recovered. Therefore, we believe new defense mechanisms should be developed to protect training against the GPU side-channel. The following figure depicts our novel attack model. This work is accepted in the 50th IEEE/IFIP International Conference on Dependable Systems and Networks (DSN 2020), 2020.
In another works, we investigate cloud-based FPGA accelerators under the model-stealing attack, which would leak model secret from cloud clients. In particular, we prove that by implementing on-chip RO-based power monitors running with other clients on the shard FPGA, the power consumption of CL(Custom Logic) of victims can be extracted remotely. Our work demonstrates that all layers and hyper-parameters of DNN models can be reconstructed by remote power side-channel analysis with high accuracy. This attack would bring in a drastic disaster since the customized structure of DNN models is considered highly valued intellectual properties for AI companies. The following figures shows our adversary model.
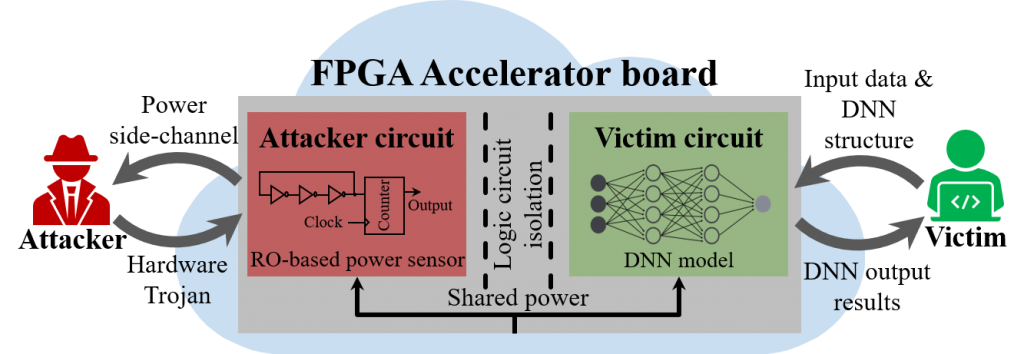
Research Area 4: Security in Additive Manufacturing Systems
Arnav Vaibhav Malwade (contact person), Shih-Yuan Yu
In cyber-physical systems, due to the tight integration of the computational, communication, and physical components, most of the information in the cyber-domain manifests in terms of physical actions (such as motion, temperature change, etc.). This leads to a system being prone to physical-to-cyber domain attacks that affect confidentiality. Physical actions are governed by energy flows which may be observed. Some of these observable energy flows unintentionally leak information about the cyber-domain and hence are known as the side-channels. Side-channels such as acoustic, thermal, and power allow attackers to acquire the information without actually leveraging the vulnerability of the algorithms implemented in the system. Our works include a wide range of different confidentiality, availability, and integrity attacks in cyber-physical additive manufacturing systems by exploring different side-channels.
In one of our works, we have taken fused deposition modeling based 3D printer to demonstrate how the acoustic side-channel can be used to breach the confidentiality of the system. In 3D printers, geometry, process, and machine information are the intellectual properties, which are stored in the cyber domain (G-code). We have designed an attack model that consists of digital signal processing, machine learning algorithms, and context-based post-processing to steal the intellectual property in the form of geometry details by reconstructing the G-code and thus the test objects. The following figure depicts our novel attack model in additive manufacturing systems.
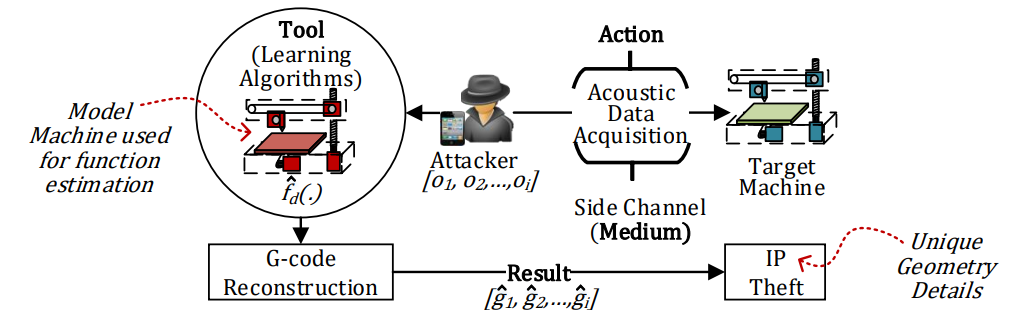
- A brief video presentation on an acoustic side-channel attack in additive manufacturing systems (e.g., 3D-printer) is given below:
Research Area 5: Security of DNA Synthesis Machine
Sina Faezi (contact person), Arnav Vaibhav Malwade
Synthetic biology is developing into a promising science and engineering field. One of the enabling technologies for this field is the DNA synthesizer. It allows researchers to custom-build sequences of oligonucleotides (short DNA strands) using the nucleobases: Adenine (A), Guanine (G), Cytosine (C),
and Thymine (T). Incorporating these sequences into organisms can result in improved disease resistance and lifespan for plants, animals, and humans. Hence, many laboratories spend large amounts of capital researching and developing unique sequences of oligonucleotides. However, these DNA synthesizers are fully automated systems with cyber-domain processes and physical domain components. Hence, they may be prone to security breaches like any other computing system. In our work, we present a novel acoustic side-channel attack methodology that can be used on DNA synthesizers to breach their confidentiality and steal valuable oligonucleotide sequences. The following figure depicts our novel attack model of the DNA synthesis machine.
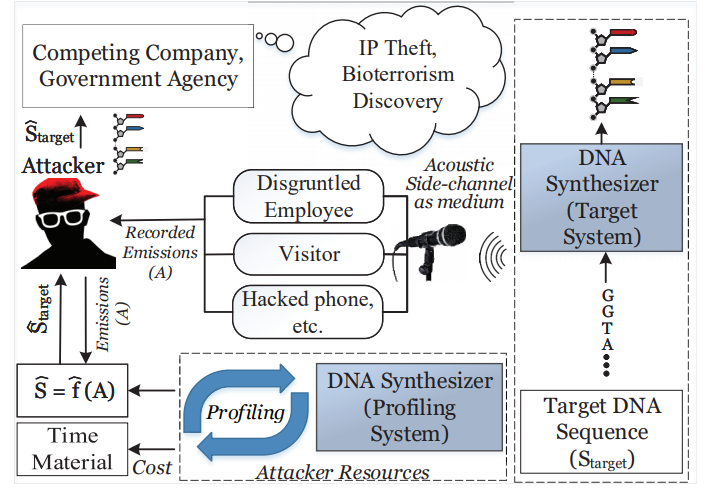
Two short video presentations on this work is given below:
Research Area 6: Automotive Security
Today, most of the innovation in the automotive domain is in electronics and software. All new features in modern cars—like advanced driver assistance systems—are based on electronics and software rather than on mechanical engineering innovations. A modern high-end car has over 100 million lines of code and it is widely believed that this number will continue to grow in the near future. Such code implements different control applications spanning across various functionalities—from safety-critical functions, to driver-assistance and comfort-related ones. These applications run on a distributed electronics and electrical (E/E) architecture, consisting of often hundreds of programmable electronic control units (ECUs) that communicate via different types of communication buses like CAN, FlexRay, LIN, and more recently also automotive Ethernet. Our research works include a wide range of automotive security applications, ranging from battery management systems to physical layer cryptographic channel utilization for V2X communication.
In one of our works, we address the key generation and management for secure automotive V2x wireless communication. This work aims to help solve the security challenges by presenting a practical key generation technique based on the reciprocity and high spatial and temporal variation properties of the automotive wireless communication channel. Accompanying this technique is also a key length optimization algorithm to improve performance (in terms of time and energy) for safety-related applications constrained by small communication windows. The following figure summarizes the proposed scheme for securing automotive wireless communication.
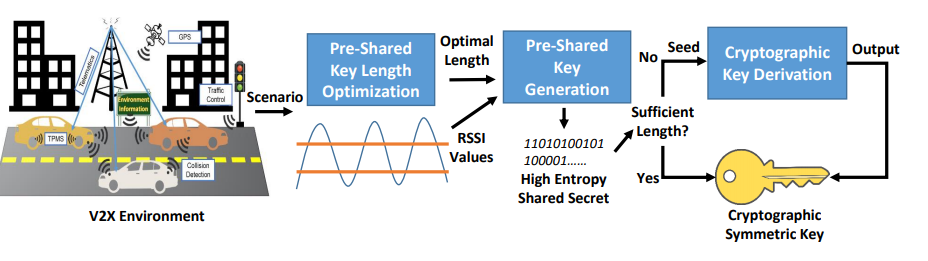
- A short video presentation on the physical layer cryptographic key generation for V2X Communication is given below:
- A short video presentation on our current work on Autonomous Vehicle Testbed built by our undergraduate students is given below:
Miscellaneous
In addition to the above research areas, our works involve security in a wide range of embedded and cyber-physical systems including:
- Security in different industrial controllers
- Security in Programmable Logic Controllers (PLCs)
- Security in Transportation systems
- Security in Battery Management systems
- Security in Machine Learning
- and many more……
